Stealthy manipulation of navigation systems
Introduction
Global Positioning System (GPS) has become an integral part of our daily lives, guiding everything from smartphones to critical infrastructure systems like aviation, military operations, and global shipping. It's one of those invisible technologies that we take for granted—until it goes wrong. However, as the use of GPS continues to expand, so do the potential threats. One particularly insidious threat is GPS spoofing, a technique that allows an attacker to manipulate or falsify GPS signals. With the ongoing geopolitical tension, notably the Russia-Ukraine conflict, GPS spoofing has become a tool in modern warfare, enabling adversaries to disrupt, deceive, or mislead the positioning systems of their opponents.
This blog post explores the vulnerabilities of GPS technology and dives deeply into the concept of GPS spoofing. Drawing from the "All Your GPS Are Belong To Us: Towards Stealthy Manipulation of Road Navigation Systems" whitepaper (27th Usenix Security 2019), we’ll discuss how spoofing attacks are executed, their potential consequences, and why this issue remains relevant in today’s world of heightened global conflicts.
How does GPS work?
GPS is a satellite-based navigation system that enables devices to determine their location, velocity, and time synchronization anywhere on Earth. It operates through a constellation of at least 31 satellites orbiting about 20,000 kilometers above Earth. While the basic idea of GPS is straightforward, the system's precision relies on some complex science, including corrections for time dilation from Einstein's general relativity and constant monitoring of Earth’s movements.
Here’s how it works:

- Satellite transmission: Each GPS satellite transmits a signal that includes its position and the exact time the signal was sent. This signal travels at the speed of light and reaches GPS receivers on the ground, which use it to calculate the time delay.
- Triangulation: For a GPS receiver to determine its location, it needs signals from at least four satellites. Using the time delay between when the signal was sent and when it was received, the receiver calculates its distance from each satellite. With at least four distance measurements, it can "triangulate" its exact location. Each GPS satellite transmits signals on the same frequencies, but these signals are modulated using different codes, allowing identification through Code Division Multiple Access (CDMA). For each visible satellite, the receiver calculates the time difference between the moment a signal is received and when it was transmitted. Along with the transmission time, satellites also broadcast important data such as the almanac and ephemeris, which describe satellite orbits. To determine the receiver's position, we must solve four unknowns: x, y, z (the coordinates in space) and t (the timing error). This requires a minimum of four equations, one from each satellite. In basic, simplified words.
- Positioning calculation: Once the GPS receiver knows its distance from several satellites, it draws imaginary spheres around each one based on the distance calculated from the signal. The intersection of these spheres pinpoints the receiver's position.
- Time and synchronization: Precise timekeeping is critical to GPS accuracy. Each satellite is equipped with atomic clocks, which are incredibly precise. However, because GPS satellites orbit high above Earth and move quickly, time passes differently for them compared to Earth-bound observers. This is where Einstein’s general relativity comes into play.
Relativistic corrections: According to general relativity, time passes more slowly the closer you are to a massive object, like Earth. The satellites are farther from Earth’s gravitational field and experience time slightly faster than we do on the surface. In contrast, the satellites also move quickly in orbit, which causes a small slowing of time according to special relativity. These two effects combine to cause a time discrepancy of about 38 microseconds per day. Without correcting for this difference, GPS positions would drift by as much as 10 kilometers daily! The GPS system includes built-in corrections for these relativistic effects, ensuring the accuracy of the positioning data.
Corrections for earth’s movements: The Earth itself isn’t a static reference point; it’s constantly in motion. This includes the rotation of the Earth, slight wobbles, tectonic shifts, and even movements caused by the Moon’s gravitational pull. Another important factor is the movement of fixed stars that help astronomers track Earth’s motion, which also feeds into GPS correction systems. Large-scale geological events like earthquakes can shift entire regions by several meters in an instant. GPS systems incorporate real-time geophysical data, including information from Very-long-baseline interferometry (VLBI), which uses distant stars to monitor how Earth's position changes in space. By tracking the positions of specific stars over time, scientists can detect minute shifts in Earth's rotation and orientation, known as polar motion. The GPS system must also correct for the slowing down of signals as they pass through Earth’s atmosphere. The ionosphere (the outermost layer of Earth’s atmosphere) can slow or bend the signal, especially during solar storms, which can throw off calculations. Correction models, constantly updated by ground-based monitoring stations, help GPS compensate for these variations.
Incorporating these complexities—relativistic time dilation, geophysical corrections, and even atmospheric interference—ensures that GPS maintains its remarkable precision. With the right adjustments, the system is accurate to within a few meters, and in some specialized cases, even down to a few centimeters (military segment). These incredible technologies highlight just how sophisticated GPS is, far beyond the simple idea of "satellites telling us where we are."
Vulnerabilities
Despite its widespread use and reliability, the GPS system is not immune to vulnerabilities. One of the main weaknesses arises from the fact that GPS signals are transmitted from satellites at very low power—around 20 watts. By the time these signals reach Earth, they are so weak that they can easily be overwhelmed by stronger signals. This makes GPS susceptible to jamming, where an attacker floods the area with noise to prevent GPS receivers from locking onto satellite signals. Another significant threat is GPS spoofing, where false signals are broadcast to deceive receivers into believing they are in a different location.
GPS jamming has become a special tool for military operations and its significancy emerged in todays world. Current situation of GPS interference can be checked eg. here: https://gpsjam.org
Additionally, GPS relies on accurate timing, and timing spoofing can disrupt synchronization in critical infrastructure systems like power grids and financial markets. The fact that GPS satellites have predictable orbits also makes them vulnerable to orbit prediction attacks, where attackers exploit their known trajectories. Finally, while encryption helps secure military GPS systems, civilian GPS signals are often unencrypted, leaving them more exposed to interference or manipulation. These vulnerabilities highlight the need for robust countermeasures, particularly in sensitive areas like national defense, aviation, and maritime operations.
One may think that GPS spoofing is only available for big players. Well...
GPS spoofing method for dummies
Because of a lack of encryption and well-known signal format there is a possibility of broadcasting a false GPS signal—either a modified one or a real signal with a delay. A spoofed signal causes the attacked receiver to calculate an incorrect location. GPS spoofing typically follows two phases: the takeover phase and the actual manipulation phase. During the takeover, the attacker gains control of the receiver (mainly because of stronger signal than the real one), and in the manipulation phase, they alter the receiver's perception of its location.
Two basic methods for the "takeover" phase
- Brute-forced takeover
+ Easy to execute
- Noticeable - Smooth takeover
+ Quiet (stealthy)
- Requires specialized equipment
What can be done?
An advanced form of GPS spoofing can be intelligent GPS spoofing, where the false location matches the physical limitations of the road. The typical victim might be a driver using a navigation app or an autonomous vehicle. The goal of the attack is to conduct a "silent" takeover, manipulating the target using only a falsified GPS signal.
- Assumption 1: The attacker knows the victim's approximate destination or parts of their actual route.
- Assumption 2: The victim is in an unfamiliar environment and relies heavily on the GPS system.
Possible objectives for the attacker:
- Change of route: The attacker seeks to confuse the victim without a specific endpoint in mind.
- Change of destination: The attacker wants to lead the victim to a predetermined location.
- Create a dangerous situation: The attacker intends to lead the victim into a hazardous situation.
Device setup
The spoofing device should be as inexpensive as possible. It should have the ability to connect via SSH and send a false GPS signal (with a specific fake location) in real-time. It has been observed that two types of attacks are possible: one where the spoofer is inside the victim's car, and one where the spoofer is in the attacker's vehicle, close to the victim. The device is just Raspberry Pi with mobile charger and connected plug-in HackRF One SDR module with additional long distance antenna. The cost of a portable spoofer is approximately $223, and it is capable of overcoming the car's bodywork even at a distance of 40-50 meters without losing signal connection.
Example of an attack
One possible attack method involves causing a "jump" in the victim's location to a nearby point from which a false path to their destination can be created on a real road. The victim usually views the map from a first-person perspective in navigation systems, so the attack might not raise suspicion. After switching to a false location, the attacker can either maintain the fake position based on observations of the victim's true movements or iteratively falsify the location to match real-world dynamics.
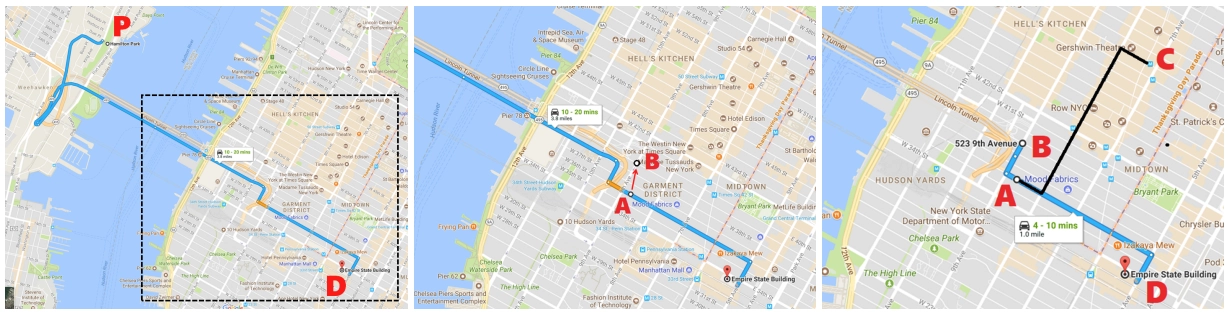
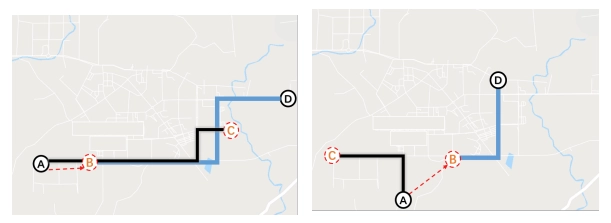
A - B: GPS spoofed and calculated location jump
B - D: Recalculated (not real) path to the victims destination
A - C: Actual path triggered by attacker
Algorithm
Input data:
- Environment description: - graph describing road network
- Victim's current location: - GPS coordinates
- Victim's desired location: - GPS coordinates
- Target destination: - The attacker's desired endpoint for the victim
Output data:
- Phantom routes: Routes that appear plausible to the victim but ultimately lead to the attacker’s target destination.
Two phases of operation:
- Initial construction of road network: The road network of the attack area is built once based on publicly available data (e.g., from OpenStreetMap) to create a graph.
- Real-time attack phase: Searching for possible attack opportunities:
- Using Google Maps API to determine the true route of the victim.
- Finding all possible false locations within a short distance from the victim's current location (matching the attack assumptions).
- Calculating, for each false location, a potential false route to the victim's target destination.
- Verifying if the false routes overlap with the actual road model and meet the attack criteria.
- Returning the result of the possible false location and route.
- Iterating the process as the victim’s location updates in real-time.
Attack testing phases
Simulation tests
The simulation tests utilized maps of Manhattan and Boston, showcasing two distinct types of road networks. The dataset consisted of 600 real taxi routes (300 from each city). For every route, all possible false locations and phantom routes were determined.
Calculations were performed on a machine with 192 GB of RAM and 24 cores.
Results:
- On average, each route allowed for 335 different attacks.
- The iterative algorithm (with two iterations) identified significantly more, averaging 3,507 attacks per route.
- Approximately 92% of routes enabled the victim to drive in circles.
- Only one route lacked the potential to put the victim in a dangerous situation.
- Searching for a single candidate for a false location took an average of 0.2 ms for Manhattan and 0.3 ms for Boston.
- The iterative attack took longer on average: 0.13 seconds for Manhattan and 0.32 seconds for Boston.
- Overall, searching through one route took about one minute.
- An attacker familiar with the victim's true route could search for a false location even before the victim reached the attack site.
Real-world environment tests
In the real-world tests, an attack type known as same-car was performed, with the spoofer located in the victim's car. One of the authors acted as the driver using Google Maps, while another operated the spoofer from the back seat using a laptop. Two different routes were tested: on-route attack and off-route attack.
Tests with unaware "volunteers"
This phase focused on understanding how users interact with GPS navigation systems, determining the conditions under which GPS spoofing attacks are most likely to succeed, and gathering user opinions on GPS spoofing. Participation in the study was divided into three parts:
- Survey section
- Driving tests
- Final interviews
Throughout the study, participants were not made aware of the potential GPS spoofing attacks.
User navigation and driving habits:
- Users were more likely to rely on GPS systems in unfamiliar environments.
- They tended to trust verbal and visual instructions more than textual ones.
Reaction to GPS spoofing attacks:
- Only 2 out of 40 participants detected at least one attack during the four routes.
- All participants noticed a loss of GPS signal during the takeover phase, but none considered this as harmful.
Opinions:
- The majority of participants admitted to experiencing faulty performance of navigation systems.
- Only 8 participants could explain the functioning of GPS spoofing.
Solutions?
As GPS spoofing attacks pose significant risks to navigation systems, implementing effective countermeasures is crucial. What can be done?
- Encryption of civilian signals: Enhancing the security of GPS signals through encryption or signal authentication can make spoofing more challenging. Very unlikely.
- Modification of receivers: Upgrading receivers to estimate the location of the transmitter based on the angle of signal arrival can improve accuracy and resistance to spoofing.
- Sensor fusion: Integrating data from other navigation systems such as Galileo and GLONASS, along with inertial measurement units (IMUs), can provide a more reliable position fix and reduce reliance on GPS alone.
- Vision-based localization: Utilizing computer vision systems to corroborate GPS data can enhance location accuracy, especially in urban environments where GPS signals may be compromised.
- Implementation of anti-spoofing algorithms: Developing sophisticated algorithms that can detect anomalies in GPS signal patterns can alert users to potential spoofing attempts.
- Awareness and training: Educating users about the risks of GPS spoofing and training them to recognize signs of tampering can help mitigate the impact of such attacks.
- Multi-frequency signals: Using multi-frequency signals can provide more robust data, as attackers may find it more challenging to spoof signals across multiple frequencies. Still - this is not a final and robust solution but only some additional difficulty for attackers.
Jokingly, according to the presented algorithm - prevention can be done also by not dense enough road networks. In Poland, roads often do not have any particular deterministic pattern. Because of that the algorithm can have some hard time finding relevant ghost locations ;)
As for now (09.10.2024), there are some complex solutions for the pointed problem. Eg. Zephr Technology approaches GPS spoofing with distributed computation and collective knowledge. Because, it is more difficult to spoof multiple devices at once - we can call it high availability system.
Conclusion
GPS spoofing remains a critical threat to navigation systems, particularly as reliance on these technologies increases in various sectors, from autonomous vehicles to smartphone applications. The experiments conducted highlight the potential vulnerabilities within GPS infrastructure and underscore the necessity for robust countermeasures. By implementing a combination of encryption, sensor fusion, and user education, we can significantly mitigate the risks posed by GPS spoofing. As we continue to advance in navigation technology, prioritizing security will be essential to ensure safety and reliability in an increasingly connected world.
References:whoami
Julian 'jul3x' Prolejko
Software Engineer
Software engineer specializing in creating low-latency systems and scalable distributed systems. Throughout my programming journey, I have worked on projects involving both low-level robotic applications and web systems, as well as automation.
My coding journey started in the web development industry. Since then I gained extensive experience in designing IT solutions and user interfaces. For over 10 years, I have been delivering modern software and customer-friendly web applications.
You can find contact details inside this personal portfolio which documents some of the projects that I created and contributed to during my lifetime.


